
"The best bitcoin is the one you store yourself"
CAUTION: Only read if you are serious about bitcoin cold storage :-)
GUIDELINES
HOW TO DO IT
NOTE TO READER
These pages give you the instructions to work out the passwords to the ‘TrueCrypt pdf files’ and ‘password protected pdf files’ which I have buried somewhere. Do not reveal these passwords to anyone. These pages also reveal the general co-ordinates of where I have buried the usb containing these files.
CODED DATA BELOW
INSTRUCTION 1: Answer the following questions.
1. What is the random 64 character password I included on my will to you?
2. What is the name of the street I lived in when I was 6 – 17 years old? (spell as ‘street’ not ‘st’)
3. What are the birthday’s of all 7 members of our immediate family from youngest to oldest in this format DDMMYYYY?
4. What is the first name of our first pet dog we ever had roughly starting around 2012? (official name not nickname)
5. What is the name of the primary school I studied at during grades 1-6? (first word only)
6. What is my full legal name as of 2017?
7. What is my city of birth as shown on my passport?
INSTRUCTION 2: Put the answers together in the right order. Replace all capital letters by their lowercase equivalent (we don’t want any capital letters). Remove all spaces between the words (we don’t want any spaces).
INSTRUCTION 3: Use the ‘QuickHash-Windows-v2.6.9.2’ program on this usb that came from https://quickhash-gui.org/download/quickhash-v2-6-9-2-for-windows/ and create a SHA512 hash of these characters. A SHA512 hash is a character string consisting of exactly 128 letters and numbers which is calculated by applying the SHA512 mathematical function to another character string. Only use the program on this usb to do this and not online SHA512 websites to do it. The reason is the online websites may record your answers or passwords. In Linux Mint 18.1: in main menu of ‘QuickHash-Windows-v2.6.9.2’, in the ‘Text’ tab under ‘Hash Algorithm’, select SHA512 > enter the characters into the ‘Text Hashing’ box > SHA512 hash result is displayed on the bottom of program.
INSTRUCTION 4: When this is complete, record the SHA-512 hash of your character string on a computer text document. We will call this the SHA512 hash (1).
INSTRUCTION 5: Now take this SHA512 hash (1) and create another SHA512 hash of the characters which we will then call SHA512 hash (2). Record this on the same computer text document as before.
INSTRUCTION 6: Now put SHA512 hash (1) and SHA512 hash (2) side by side (SHA512 hash (1) goes first). Remove all the letters in these two SHA512 hashes to leave only the numbers.
You should now be left with a number with 154 digits. The LAST 4 numbers should be 4661.
INSTRUCTION 7: Record the first 148 numbers into a straight line onto a piece of paper with large gaps between each of the numbers. You could also use a computer ‘Text File’ to record the numbers. Double check you have entered them correctly.
INSTRUCTION 8: Now do the following (or add the following) to each of the 148 numbers individually and write the answers down onto the piece of paper or into the computer ‘Text File’. Double check you have done the maths correctly.
-1 +1 -3 -1 -8 -4 -4 +4 -3 +2 +3 -4 -7 +3 -5 +1 +2 +0 -5 +2 +1 +0 +2 +9 +1 +0 -3 +1 +3 +0 -6 -3 +0 +1 -1 -4 +4 -6 -2 -3 -1 -7 -3 +4 -3 +2 -1 -7 +0 -2 +0 -1 -6 -7 -1 +1 +5 -2 -1 -3 -2 -1 -6 -2 +8 -2 -6 -6 +5 +2 +3 +6 +0 +2 -9 -8 -8 +8 -6 +4 -7 +1 +3 +4 +6 +0 +5 -6 -4 -3 +4 +1 -3 +0 -2 -1 +2 -6 +3 +1 +5 -2 +1 +0 -5 -5 -6 +4 -1 -5 -1 -6 -5 -2 -4 -1 -2 +4 -4 +4 +1 -8 -2 +1 +2 -5 +0 +3 -6 -1 +4 -3 -4 -1 -1 -1 -1 +3 +1 -4 +1 -2 +3 -3 -3 +0 +2 +0
NOTE: A possible way to accurately perform these conversions is to enter (or copy and paste) the INSTRUCTION 7 numbers onto a ‘LibreOffice Calc’ document within Linux Mint (into cell A1, B1, C1, D1 and so on and so forth) and then below this copy and paste (select ‘Paste Special...’ then ‘Unformatted text’) the above INSTRUCTION 8 number codes into the row directly below the INSTRUCTION 7 numbers (into cell A2, B2, C2, D2 and so on and so forth). After this, create a Formula function in Cell A3 such that the number in Cell A1 is added to the number in Cell A2 (ie. type into Cell A3 ‘=A1+A2’). After this click and hold your mouse pointer on the bottom right hand corner of Cell A3 and drag it to the right hand side, passing by all the cells with numbers above them. This will calculate for you all the numbers. For your information, the number codes above in INSTRUCTION 8 have the [TAB] key pressed before each number to enable copy and paste into ‘LibreOffice Calc’, so if you want to copy and paste the INSTRUCTION 7 numbers into ‘LibreOffice Calc’ you will also need to add the [TAB] key before each number.
INSTRUCTION 9: You now have the 148 numbers to the following pieces of information:
Numbers 1 to 64 = 64 numbers-only base password to allow you to open the ‘password protected pdf file’ inside the ‘TrueCrypt pdf file (version B)’ that is on a Usb that has been buried somewhere. The ‘password protected pdf file’ contains the electrum seeds, and public and private addresses to all my Bitcoins.
Number 65 = Either a number eight (8) that is used to represent a ‘+’ sign (OR) a number nine (9) that is used to represent a ‘-’ sign.
Numbers 66 – 83 = 18 numbers that (together with the + or – symbol from Number 65) are the ‘general’ co-ordinates of where I have buried the Usb containing the computer files which contain all my Bitcoin information. These are only general co-ordinates and not exact coordinates. They are represented in this format:
+/- _ _ . _ _ _ _ _ _ , +/- _ _ _ . _ _ _ _ _ _
The place where it says +/- above is represented by (8) for + and (9) for -.
Simply do an internet search on these co-ordinates to find out where it is. For example, the co-ordinates below are the co-ordinates for the Opera House in Sydney.
33°51'24.6"S 151°12'54.0"E
-33.856831, +151.215005
For this example your INSTRUCTION 9 decoded co-ordinate numbers 65 - 83 would be:
9338568318151215005
Number 84 = One number seven (7) that is used as a separator
Numbers 85 – 148 = 64 numbers-only password to an email TrueCrypt pdf file I have emailed to the following email addresses:
person1@emailaddress1.com
person1dropbox@emailaddress1.com
person1@emailaddress2.com
person1dropbox@emailaddress2.com
person2@emailaddress1.com
person2dropbox@emailaddress1.com
person2@emailaddress2.com
person2dropbox@emailaddress2.com
person3@emailaddress1.com
person3dropbox@emailaddress1.com
person3@emailaddress2.com
person3dropbox@emailaddress2.com
person4@emailaddress4.com
person4dropbox@emailaddress4.com
myemailaddress1@myemailddress1.com
myemailaddress1dropbox@myemailadress1.com
myemailaddress2@myemailddress2.com
myemailaddress2dropbox@myemailadress2.com
myemailaddress3@myemailddress3.com
myemailaddress3dropbox@myemailadress3.com
31st of January 2017
myemailaddress1@myemailaddress1.com
_____
____
Please, please do not delete or save onto your computer. Please only open if allowed, using the password in my safe deposit box. The information on this usb is strictly for your viewing only and is strictly for storage here
This emailed ‘TrueCrypt pdf file’ contains a ‘password protected pdf file’ that contains the coded data revealing the ‘exact’ co-ordinates of where I buried the Usb containing all my Bitcoin information.
>>> End of Doc <<<
Note: The above sample values highlighted in green were derived from the following answers to the security questions: Question 1: 2641152251515664112664345515363152263421343412266535622421311645 Question 2: Kayak Alley Question 3: 18042007020920041010200215051999040919971705197227111970 Question 4: Pluto Question 5: Theodore Question 6: Giovanna Carson Galvin Question 7: San Francisco
Step 1.2: Copy and paste the above ‘sample coded data’ onto a New Office Document (Microsoft word document, WPS writer document or any other document format that retains the correct formatting when copied onto). After this is done, save this file on Usb No. 10. You will be using this template to create your own ‘coded data’ bank safe deposit box document.
Step 2: Study the following sample ‘Coded Data’ that will be stored at the email addresses listed in the first bank safe deposit box coded data sheet
Step 2.1: Study the following text so you understand how this method works
>>> Start of Doc <<<
NOTE TO READER
These pages give you the instructions to work out the ‘exact’ co-ordinates to the ‘TrueCrypt pdf files’ and ‘password protected pdf files’ which I have buried somewhere. Do not reveal these co-ordinates to anyone.
CODED DATA BELOW
INSTRUCTION 1: Take the first 30 numbers that were written in INSTRUCTION 8 of the coded data sheet that was in the bank safe deposit box. Do not take the numbers you calculated that are part of the password to the buried usb files. Take the numbers recorded in INSTRUCTION 8 with the plus and minus signs. Take these numbers but ignore all the plus or minus (+/-) signs. Don’t include spaces or anything else. Save these 30 numbers in a computer text document.
INSTRUCTION 2: Take the first 2 email addresses recorded in INTRUCTION 9 of the coded data sheet that was in the bank safe deposit box. Put both email addresses side by side in the right order (first to last). Do not include spaces. Change all the capital letters to lower case letters. Save these two email addresses in the same computer text document as before.
INSTRUCTION 3: Take the answers to the first 4 security questions in INSTRUCTION 1 of the coded data sheet that was in the bank safety deposit box. Do not include spaces. Change all the capital letters to lower case letters. Save these answers in the same computer text document as before.
INSTRUCTION 4: Use the ‘QuickHash-Windows-v2.6.9.2’ program on this usb that came from https://quickhash-gui.org/download/quickhash-v2-6-9-2-for-windows/ and create a SHA512 hash of all the characters you saved in the computer text document in the exact right order (INSTRUCTION 1 first, INSTRUCTION 2 next, INSTRUCTION 3 last). A SHA512 hash is a character string consisting of exactly 128 letters and numbers which is calculated by applying the SHA512 mathematical function to another character string. Only use the program on this usb to do this and not online SHA512 websites to do it. The reason is the online websites may record your answers or passwords. In Linux Mint 18.1: in main menu of ‘QuickHash-Windows-v2.6.9.2’, in the ‘Text’ tab under ‘Hash Algorithm’, select SHA512 > enter characters into the ‘Text Hashing’ box > SHA512 hash result is displayed on the bottom of program.
INSTRUCTION 5: When this is complete, record the SHA-512 hash of your character string on a computer text document. We will call this the SHA512 (1) hash.
INSTRUCTION 6: Remove all the letters in the SHA512 (1) hash to leave only the numbers.
You should now be left with a number with 76 digits. The LAST 4 numbers should be 7935.
INSTRUCTION 7: Record the first 59 numbers into a straight line onto a piece of paper with large gaps between each of the numbers. You could also use a computer ‘Text File’ to record the numbers. Double check you have entered them correctly.
INSTRUCTION 8: Now do the following (or add the following) to each of the 59 numbers individually and write the answers down onto the piece of paper or into the computer ‘Text File’. Double check you have done the maths correctly.
+3 -1 -7 -7 +3 +7 +3 -3 +2 +6 -2 -8 -1 +1 -1 +7 -5 +1 +3 -2 +3 +4 +0 +8 -3 +2 -7 +4 -1 +7 -2 -2 -6 -7 +5 +0 -4 +3 +3 -2 +5 +2 -4 +3 +1 -6 +6 +5 +7 +8 -7 -7 -4 -3 +4 +5 -3 +7 +6
NOTE: A possible way to accurately perform these conversions is to enter (or copy and paste) the INSTRUCTION 7 numbers onto a ‘LibreOffice Calc’ document within Linux Mint (into cell A1, B1, C1, D1 and so on and so forth) and then below this copy and paste (select ‘Paste Special...’ then ‘Unformatted text’) the above INSTRUCTION 8 number codes into the row directly below the INSTRUCTION 7 numbers (into cell A2, B2, C2, D2 and so on and so forth). After this, create a Formula function in Cell A3 such that the number in Cell A1 is added to the number in Cell A2 (ie. type into Cell A3 ‘=A1+A2’). After this click and hold your mouse pointer on the bottom right hand corner of Cell A3 and drag it to the right hand side, passing by all the cells with numbers above them. This will calculate for you all the numbers. For your information, the number codes above in INSTRUCTION 8 have the [TAB] key pressed before each number to enable copy and paste into ‘LibreOffice Calc’, so if you want to copy and paste the INSTRUCTION 7 numbers into ‘LibreOffice Calc’ you will also need to add the [TAB] key before each number.
INSTRUCTION 9: You now have the 59 numbers to the following pieces of information:
Number 1 = Either a number eight (8) that is used to represent a ‘+’ sign (OR) a number nine (9) that is used to represent a ‘-’ sign.
Numbers 2 – 19 = 18 numbers that (together with the + or – symbol from Number 1) are the ‘exact’ co-ordinates of where I have buried the Usb containing the computer files which contain all my Bitcoin information. These are the exact coordinates. They are represented in this format:
+/- _ _ . _ _ _ _ _ _ , +/- _ _ _ . _ _ _ _ _ _
The place where it says +/- above is represented by (8) for + and (9) for -.
Simply do an internet search on these co-ordinates to find out where it is. For example, the co-ordinates below are the co-ordinates for the Opera House in Sydney.
33°51'24.6"S 151°12'54.0"E
-33.856831, +151.215005
For this example your INSTRUCTION 9 decoded co-ordinate numbers 1 - 19 would be:
9338568318151215005
Number 20 = One number seven (7) that is used as a separator
Numbers 21 - 39 = a repeat of the information in Numbers 1 and Numbers 2 -19 for the second location I have buried the same copy of the usb drive with the bitcoin information.
Number 40 = One number seven (7) that is used as a separator
Numbers 41 - 59 = a repeat of the information in Numbers 1 and Numbers 2 -19 for the third location I have buried the same copy of the usb drive with the bitcoin information.
>>> End of Doc <<<
NOTE: The above sample values highlighted in green were derived from the following answers to INSTRUCTIONS 1 - 3: INSTRUCTION 1: 113184443234735120521029103130 INSTRUCTION 2: person1@emailaddress1.comperson1dropbox@emailaddress1.com INSTRUCTION 3: 2641152251515664112664345515363152263421343412266535622421311645kayakalley18042007020920041010200215051999040919971705197227111970pluto
Step 2.2: Copy and paste the above ‘sample coded data’ onto a New Office Document (Microsoft word document, WPS writer document or any other document format that retains the correct formatting when copied onto). After this is done, save this file on Usb No. 10. You will be using this template to create your own ‘coded data’ emailed document.
Step 3: Download needed programs and save to Usb X
Step 3.1 Download ‘QuickHash-Windows-v2.6.9.2’ from https://quickhash-gui.org/download/quickhash-v2-6-9-2-for-windows/ if you don’t already have a copy. Only download this specific version (Windows-v2.6.9.2) but if you can’t find it from this website, do an online search-engine search to download it from another site. If you download it from another site, check that the checksum of the file is correct (see our ‘Checksums’ page in our Security section for details). If you don’t want to use this particular program, then you can use a different SHA512 hashing software package but test it out first by comparing the results with those from other sources. Also, the result must contain capital and not lowercase letters. Copy and paste it onto Usb X.
Step 3.2: Download the ‘TrueCrypt 7.1a’ installation package for Linux operating systems from https://www.grc.com/misc/truecrypt/truecrypt.htm if you haven’t already got a copy. Only download this specific version (version 7.1a) and if you can’t find it from this website, do an online search-engine search to download it from another site. If you download from another site, check that the checksum of the file is correct (see our ‘Checksums’ page in our Security section for details). The name of the file is truecrypt-7.1a-linux-x64.tar.gz (for 64 bit machines) or truecrypt-7.1a-linux-x86.tar.gz (for 32 bit machines). Copy and paste the downloaded file onto Usb X.
Step 3.3: Download ‘Foxit Advanced PDF Editor 3.1.0.0’ from https://foxit-advanced-pdf-editor.en.softonic.com/ if you don’t already have a copy. Only use this specific version (version 3.1.0.0) and if you can’t find it from this website, do an online search-engine search and download it from another site. If you download it from another site, check that the checksum of the file is correct (see our ‘Checksums’ page in our Security section for details). Copy and paste the downloaded file onto Usb X.
Step 4: Completely format the ‘bank safety deposit box’ usb
Step 4.1: Insert the bank safety deposit box usb in a free usb port. This is the usb that will contain the ‘IMPORTANT INSTRUCTIONS…’ document containing the coded instructions with the security questions (sample of the ‘coded data’ sheet is shown in Method 6 (Variation 2): step 1). This is the usb with the minimum 128 megabyte free space when empty.
Step 4.2: Do a complete format of the bank safety deposit box usb (a complete format should be done and not a quick format). Windows 7: Right click usb drive > click ‘Format…’ > Uncheck ‘Quick Format’ > click ‘Start’ > click ‘OK’.
Step 4.3: Do a complete ‘Eraser’ format of the bank safety deposit box usb. This process can take a while so be patient. Windows 7: Right click usb drive > select ‘Eraser’ > click ‘Erase Unused Space’.
Step 5: Boot up the Zorin OS Core usb operating system you used to create your Bitcoin addresses in the TrueCrypt pdf file.
Step 5.1: Boot up the Zorin OS Core usb operating system from Usb No. 9. This is the same operating system you used to create your Bitcoin addresses in the TrueCrypt pdf file. See Method 3: steps 3.1 to 3.4 if you don’t remember how to do this.
From this step onwards, an internet connection is not needed and you should remain disconnected from the internet for the entire time you are using the Zorin OS Core operating system.
Step 6: Create a ‘Public-Addresses-Only’ pdf document of your TrueCrypt pdf file, if you don’t already have one
Step 6.1: Open the ‘LibreOffice Writer’ document where you will be saving the bitcoin public addresses. Create a heading for the document with the name of the wallet file it came from such as ‘3 Jan 2017 Linux Wallet A’ and the words ‘Public Addresses Only’ directly underneath it.
Step 6.2: Load up the Electrum portable program again from the usb and open the wallet file you want to extract the public addresses from. Zorin OS Core: Double click ‘electrum program’ > click ‘File’ > click ‘Open’ > search for ‘wallet file’ > press ‘Open’.
Step 6.3: Now click ‘Wallet’ in the electrum program, move your mouse down to ‘Private keys’, then press ‘Export’. Enter your password, then click ‘OK’.
Your wallets public and private keys (or addresses) will now be revealed.
Step 6.4: Keeping the default ‘Format’ settings of ‘CSV’, click ‘on ‘File’, then change the folder location to ‘Desktop’ at the very top of the options, then click ‘Save’. After this click ‘Export’ and then ‘OK’.
Step 6.5: Now search on your Desktop for the ‘electrum-private-keys.csv’ file you just created and double click on it to open with ‘LibreOffice Calc’.
Step 6.6: Click ‘OK’ on the first screen. Then highlight all the ‘Public addresses’ under where it says ‘address’, then copy and paste these onto a newly opened ‘Text File’ before copying and pasting it again from the ‘Text File’ onto your ‘LibreOffice Writer’ document.
When this is all done your document should look something like this.

Step 6.7: Save this LibreOffice document in Microsoft Word 97-2003 (.doc) format.
If you would like to create more than one set of public addresses; in the Electrum program repeat this process (steps 4.2 – 4.7) for all your electrum wallets. When you are finally finished…
Step 6.8: Select ‘File’ in the main menu on the top of LibreOffice Writer, then select ‘Export as PDF...’ and then press ‘Export’, then press ‘Save’. A new pdf file should now appear on your desktop. Close LibreOffice and all other unnecessary windows/folders. Then copy and paste the pdf document to the spare Usb (which is Usb No. 8 if you arrived here from Step 3 of this method).
NOTE: You can include the ‘Master Public Key’ in this Public-Addresses-Only pdf document if you like. Including it will make it easier for you to track all the bitcoin addresses in the wallet if more than the default number have been used. There is however a known weak point where if both a single ‘private key’ is known and the ‘master public key’ is known, the seed can be calculated. For this reason, if you choose to go ahead and include the ‘Master Public Key’ then add a warning like:
WARNING: ANYONE WHO KNOWS A SINGLE PRIVATE kEY OF ONE OF THESE PUBLIC ADDRESSES + THIS MASTER PUBLIC KEY, CAN WORK OUT YOUR SEED FOR THIS WALLET
Step 7: Calculate or re-calculate the passwords to your buried Master usb containing the TrueCrypt pdf file (version B) with all your bitcoin information (seeds, public and private addresses).
Step 7.1: Following Method 5: steps 1.6 – step 1.12, calculate your 64 numbers-only base Master usb password so you know what it is as you will be needing it to create the coded data document with the security questions.
Step 8: Prepare the ‘coded data’ electronic text document with the security questions to be stored in the bank safe deposit box (see ‘Choosing security questions’ article in the Security section for more information on how to choose security questions).
Step 8.1: Create the 64 numbers-only dice generated base password to emailed TrueCrypt pdf files by following Method 6 (Variation 2): step 10.1.
Step 8.2: Following the template from Method 6 (Variation 2): step 1, prepare your Coded data sheet. The document template should be on Usb No. 10 when you saved it in Step 1.2. Load the document from Usb No. 10 using LibreOffice Writer.
INSTRUCTION results for sample coded data shown in Method 6 (Variation 2): step 1.1
INSTRUCTION 3 = CHARACTER RESULT FROM SECURITY QUESTIONS
2641152251515664112664345515363152263421343412266535622421311645kayakalley18042007020920041010200215051999040919971705197227111970plutotheodoregiovannacarsongalvinsanfrancisco
INSTRUCTION 4 = SHA512 (1) HASH RESULT
A6B49C6E98F4DD2C5068A83D861BC380590D0E22FFB5C44069F52B74B47D392ABAB94D43DF0F5EB818CCF3A16EA8814CD5ED5F52C5A9C8ACFCC07EF77A26FFC5
INSTRUCTION 5 = SHA512 (2) HASH RESULT
C1379FD8908D29DE023BD0F3F19E892AB06D25B718A13085566B806EB7C6DE89763415AF14A9B5F1FA465BCA3A8AF318C945E5F30F0905F26541F4044CE6A61D
INSTRUCTION 6 (PART 1) = SHA512 (1) HASH + SHA512 (2) HASH
A6B49C6E98F4DD2C5068A83D861BC380590D0E22FFB5C44069F52B74B47D392ABAB94D43DF0F5EB818CCF3A16EA8814CD5ED5F52C5A9C8ACFCC07EF77A26FFC5C1379FD8908D29DE023BD0F3F19E892AB06D25B718A13085566B806EB7C6DE89763415AF14A9B5F1FA465BCA3A8AF318C945E5F30F0905F26541F4044CE6A61D
INSTRUCTION 6 (PART 2) = NUMBERS OF SHA512 (1) HASH + SHA512 (2) HASH
6496984250688386138059002254406952744739294430581831688145552598077726513798908290230319892062571813085566806768976341514951465383189455300905265414044661
INSTRUCTION 7 = FIRST 148 NUMBERS OF SHA512 (1) HASH + SHA512 (2) HASH
6496984250688386138059002254406952744739294430581831688145552598077726513798908290230319892062571813085566806768976341514951465383189455300905265414
INSTRUCTION 8 = 148 NUMBERS AFTER CONVERSION
5565140622941637333269293225700653608116121802411630017293420436851178873900182621576363466132363244566511245252452225155132615622555344231513532434
INSTRUCTION 9 = NUMBERS 1 - 64 = 64 numbers-only base password to buried Master Usb files
5565140622941637333269293225700653608116121802411630017293420436
INSTRUCTION 9 = NUMBER 65 = + (8) or - (9) sign
8
INSTRUCTION 9 = NUMBERS 66 - 83 = general co-odinates to main location of buried Master Usb (obtained by pressing curser on location in google maps)
511788739001826215
INSTRUCTION 9 = NUMBER 84 = separator number 7 (no meaning)
7
INSTRUCTION 9 = NUMBERS 85 - 148 = 64 numbers-only dice generated base password to emailed TrueCrypt pdf files (created using Method 6 (Variation 2): step 10.1)
6363466132363244566511245252452225155132615622555344231513532434
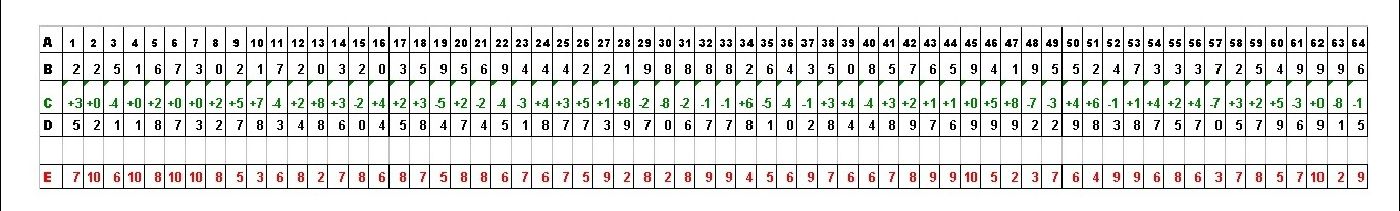
Step 8.4: To get a clearer idea of how to come up with the INSTRUCTION 8 codes, see below for another example of the first 64 digits of a SHA512 (1) hash values after the letters are removed (Row B), and the corresponding INSTRUCTION 8 +/- number codes (Row C), and corresponding 64 digit number-only passwords to the pfd files (Row D). Row E is shown for those interested but can be ignored:
Graph 1: 64 digit numbers-only password based on possible numbers (0-9)
A = Place number of 64 digits
Graph 2: 64 digit numbers-only password based on possible numbers (1-6)
A = Place number of 64 digits
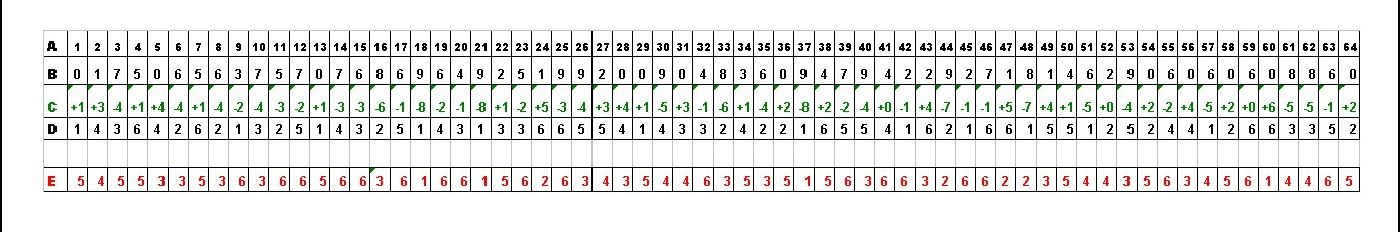
As you can see, the way to come up with the number code in green is to see how you can turn the SHA512 (1) hash number into the 64 digit number-only password number. This simply requires you to subtract the SHA512 (1) hash number from the 64 digit number-only password number. Ignore all Row E numbers in red as these numbers are only added as extra information for those who are interested in it. Take note that it may be easier for you to prepare the number codes in Linux Mint using the ‘LibreOffice Calc’ program, by adding the [TAB] key between each number after first saving the numbers onto a new ‘Text File’; and then after this, copying and pasting (select ‘Paste Special...’ then ‘Unformatted text’) all of it from the new ‘Text File’ into ‘LibreOffice Calc’.
Step 8.5: Replace all the text highlighted in green with your own questions and number values. When creating the questions, mix up the order of the questions. The number codes for INSTRUCTION 8 should have the [TAB] key pressed before each number.
Step 8.6: When complete, double check that all your values are correct by redoing it all from the beginning and pretending to be the person who will be viewing these files. Then save the document onto Usb No. 10.
Step 9: Add to ‘IMPORTANT INSTRUCTIONS FROM (your_name) – READ HERE’ document on Usb No. 10 and store it in the bank safety deposit box usb
You should have on Usb No. 10, an editable Microsoft word (or other format) document of the ‘IMPORTANT INSTRUCTIONS…’ text prepared in Method 5; but if you don’t you will need to create another one by following Method 5: step 4.1.
Step 9.1: Open this ‘IMPORTANT INSTRUCTIONS…’ Microsoft word (or other format) document in LibreOffice Writer and copy and paste the entire ‘coded data’ sheet with the security questions, you prepared in Method 6 (Variation 2): step 7, to the last page of the IMPORTANT INSTRUCTIONS…’ document. Save the new ‘IMPORTANT INSTRUCTIONS…’ document and close LibreOffice Writer.
Step 9.2: Now copy and paste from Usb No. 10 the new ‘IMPORTANT INSTRUCTIONS…’ Microsoft word (or other format) document which contains the coded data sheet from step 8, onto the Zorin OS Core desktop.
Step 9.3: Convert the ‘IMPORTANT INSTRUCTIONS…’ document you just copied to your desktop into pdf format, then save it on your desktop. Keep the non pdf version of the ‘IMPORTANT INSTRUCTIONS…’ document on the desktop. Zorin OS Core: Within LibreOffice Writer select ‘File’> select ‘Export as PDF...’> press ‘Export’ > press ‘Save’ > Then close ‘LibreOffice Writer’.
Step 9.4: Insert the blank ‘safe deposit box usb’ into a free usb port.
Step 9.5: Copy and paste both the ‘IMPORTANT INSTRUCTIONS FROM (your_name) – READ HERE’ pdf and non pdf documents (you just prepared and just saved to your desktop), onto the bank safe deposit box usb. Make sure the part of the file name above that says ‘(your_name)’ is actually your name (eg. David Bowen) and if it isn’t then rename it so it is.
Step 9.6: Copy and paste the non password protected ‘Public-Addresses-Only’ pdf document you prepared in step 6 to this bank safe deposit box usb. When complete, remove the bank safe deposit usb from your computer.
Your bank safe deposit box usb is complete and almost ready to be put in the bank safe deposit box.
Step 10: Create a secure password using dice
Step 10.1: Roll one physical dice 64 times; or roll 4 physical dice 16 times; or roll any other combination of dice to get 64 rolls. Enter these numbers into a new ‘Text file’ and save the ‘Text File’ to your free usb drive (which is Usb No. 10 if you arrived here from Step 9 of this method).
These 64 numbers is your 64 numbers-only base password you will use to create the passwords to secure your ‘password protected pdf file’ and ‘TrueCrypt pdf file’ containing the ‘coded instructions’ from Method 6 (Variation 2): step 2 which you will email.
Step 10.2: Copy and paste the ‘QuickHash-Windows-v2.6.9.2’ hashing program from Method 6 (Variation 2): step 3.1 onto the Zorin OS Core desktop and then open it from there. What this program will do is to convert any character string you enter into it, into another character string consisting of exactly 128 letters and numbers, and this new character string is called a SHA512 hash of the first character string.
Step 10.3: Use this program and create a SHA512 hash of these 64 numbers. We will call this the SHA512 (1) hash. Only use the program you have downloaded and copied onto your computer to do this and not online SHA-512 websites to do it. The reason is the online websites may record your answers or passwords. Zorin OS Core: in main menu of ‘QuickHash-Windows-v2.6.9.2’, in the ‘Text’ tab under ‘Hash Algorithm’, select SHA512 > copy and paste 64 dice rolled numbers into the ‘Text Hashing’ box > copy and paste resulting SHA512 (1) hash result displayed on bottom of program into the new ‘Text File’.
This first SHA512 (1) of the 64 dice rolled numbers is now your secure password to the ‘password protected pdf file’ that will be in ‘TrueCrypt pdf file’ containing the ‘coded instructions’ from Method 6 (Variation 2): step 2 which you will email.
Step 10.4: Take this SHA512 (1) hash of the 64 numbers-only base password and SHA512 hash it again. The result called SHA512 (2) hash will be used as the password to ‘TrueCrypt pdf file’ containing the ‘password protected pdf file’ and ‘coded instructions’ (from Method 6 (Variation 2): step 2) which you will email.
Step 10.5: Type these passwords down onto a new ‘Text File’ on Usb No. 10 and add some notes after them (such as ‘64 digit numbers-only password’ or ‘email TrueCrypt password’ or ‘password protected pdf file password’) so you know what each is. As an example, see the table below to see the passwords created from the Sample coded data shown in Method 6 (Variation 2): step 1.1.
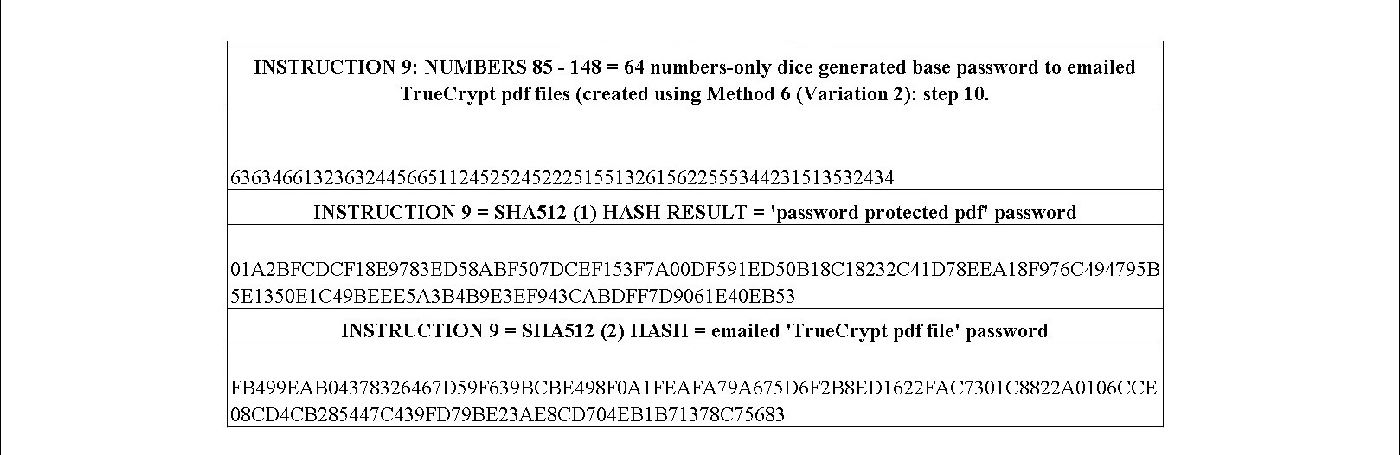
Now that you know all the correct password codes, you are ready to create the emailed ‘TrueCrypt pdf file’ containing the ‘password protected pdf file’ which reveals the exact location of your buried Master usb, and which will be emailed to the correct addresses written in the Method 6 (Variation 2): Step 1 document.
Step 11: Prepare the emailed ‘TrueCrypt pdf file’ containing the ‘password protected pdf file’ which reveals the exact location of your buried usb
Step 11.1: Following the template from Method 6 (Variation 2): step 2, prepare your Coded data sheet to be converted to an email ‘TrueCrypt pdf file’ and emailed to the chosen addresses. The document template should be on Usb No. 10 when you saved it in Step 2.2. Load the document from Usb No. 10 using LibreOffice Writer.
Step 11.2: To get a clearer idea on how it all works, see the info below for all the results of the sample data shown in Method 6 (Variation 2): Step 2.1. You can also use this info as a template to prepare your codes.
INSTRUCTION results for sample coded data shown in Method 6 (Variation 2): step 2.1
INSTRUCTION 1 = FIRST 30 NUMBERS OF INSTRUCTION 8 CODED DATA IN BANK SAFE DEPOSIT BOX (without + or - signs)
113184443234735120521029103130
INSTRUCTION 2 = FIRST 2 EMAIL ADDRESSES OF INTRUCTION 9 CODED DATA IN BANK SAFE DEPOSIT BOX (without spaces and in lower case only)
person1@emailaddress1.comperson1dropbox@emailaddress1.com
INSTRUCTION 3 = FIRST 4 SECURITY QUESTION ANSWERS OF INSTRUCTION 1 CODED DATA IN BANK SAFE DEPOSIT BOX (without spaces and in lower case only)
2641152251515664112664345515363152263421343412266535622421311645kayakalley18042007020920041010200215051999040919971705197227111970pluto
INSTRUCTION 4 & 5 = SHA512 (1) HASH
C568C841536FF3A282730550DA95B0808E6ADEE92A5122FCEFDEE894A4A8059327ECCDBC4182BD10EF0FDC7C8465A1703B596A77098DC387FEBB577AB9BDF35A
INSTRUCTION 6 = NUMBERS OF SHA512 (1) HASH
5688415363282730550950808692512289448059327418210078465170359677098387577935
INSTRUCTION 7 = FIRST 59 NUMBERS OF SHA512 (1) HASH
56884153632827305509508086925122894480593274182100784651703
INSTRUCTION 8 = 59 NUMBERS AFTER CONVERSION
85117880890018270637848858264800229443878437228678010396479
INSTRUCTION 9 = NUMBER 1 = + (8) or - (9) sign
8
INSTRUCTION 9 = NUMBERS 2 - 19 = exact co-ordinates to main location buried Master Usb (obtained by pressing curser on location in google maps)
511788089001827063
INSTRUCTION 9 = NUMBER 20 = separator number 7 (no meaning)
7
INSTRUCTION 9 = NUMBERS 21 - 39 = exact co-ordinates to 2nd location of buried Master Usb (obtained by pressing curser on location in google maps)
8488582648002294438
INSTRUCTION 9 = NUMBER 40 = separator number 7 (no meaning)
7
INSTRUCTION 9 = NUMBERS 41 - 59 = exact co-ordinates to 3rd location of buried Master Usb (obtained by pressing curser on location in google maps)
8437228678010396479
Step 11.3: Look at the examples given in Method 6 (Variation 2): step 8.4 if you don’t remember how to convert the number codes in INSTRUCTION 8 of the ‘coded data’ sheet.
Step 11.4: Replace all the text highlighted in green with your own questions and number values.
Step 11.5: When complete, double check that all your values are correct by redoing it all from the beginning and pretending to be the person who will be viewing these files. Then save the document onto Usb No. 10 into Microsoft word format.
Step 11.6: Now copy and paste from Usb No. 10 the soon to be emailed ‘Coded data’ Microsoft word document you just created, onto the Zorin OS Core desktop.
Step 11.7: Convert this soon to be emailed ‘Coded data’ Microsoft word document you just copied to your desktop into pdf format, then save it on your desktop, and then delete the non pdf version. Zorin OS Core: Within LibreOffice Writer select ‘File’> select ‘Export as PDF...’> press ‘Export’ > press ‘Save’ > Then close ‘LibreOffice Writer’ > then delete non pdf version of the ‘the soon to be emailed ‘Coded data’ Microsoft word document from the desktop.
Now that you have the ‘coded data’ in pdf format, you can add a password to it and turn it into a ‘password protected pdf file’
Step 11.8: Add the appropriate password to your ‘coded data’ pdf file that will be emailed. See Method 3: steps 7.1 - step 8.6 if you don’t remember how to do this.
Now that you have the ‘coded data’ in a ‘password protected pdf file’, you can put it in a TrueCrypt volume/drive and turn it into a ‘TrueCrypt pdf file’
Step 11.9: Place the password protected pdf file that will be emailed into a TrueCrypt volume/drive and turn it into a ‘TrueCrypt pdf file’ which will be emailed. See Method 4: steps 1.1 - step 5.9 if you don’t remember how to do this.
Step 11.10: Copy and paste the completed email ‘TrueCrypt pdf file’ from the Zorin OS Core desktop onto Usb No. 10.
Step 11.11: Create a new ‘Text File’ on Usb No. 10 and copy and paste everything you wrote under INSTRUCTION 9 of the safe deposit box coded data sheet (which you prepared in Method 6 (Variation 2): step 8). The most important thing to include is the list of email addresses you will be sending the file to and the notes below these stating the date the email is sent, sending address, email attachment name, email subject line and email text. Then save the new ‘Text File’.
Your ‘TrueCrypt pdf file’ with the ‘password protected pdf file’ containing the ‘coded instructions’ from Method 6 (Variation 2): step 2 is complete and ready to be emailed to all the correct email addresses. Delete any work-in-progress files that may be in Usb No. 10. The following files should be the only files on Usb No. 10:
‘TrueCrypt pdf file (version B)’
‘QuickHash-Windows-v2.6.9.2’
‘TrueCrypt 7.1a’ installation package
‘Foxit Advanced PDF Editor 3.1.0.0’
‘Public-Addresses-Only’ pdf document
'emailed ‘TrueCrypt pdf file’
‘IMPORTANT INSTRUCTIONS FROM (your_name) – READ HERE’ pdf and non-pdf document
‘new ‘Text File’ with INSTRUCTION 9 notes’
Step 12: Finalise and bury Master usb with the TrueCrypt pdf file (version B) - if this hasn’t already been done
Step 12.1: Tell your family (or other inheritors) roughly or exactly where you have buried or will bury the Master usb. If you haven’t yet buried it you could even bury it while they watch you.
Step 12.2: Finalize and bury your Master usb if this hasn’t already been done. To finalize it, follow ALL steps from Method 5: steps 8.1 – step 8.7. This is the actual burying part.
Congratulations, you have buried your Master Usb
Step 13: Finalise and email the email ‘TrueCrypt pdf file’
Step 13.1: Insert Usb X into one of your usb drives and copy and paste the email ‘TrueCrypt pdf file’ that is to be emailed onto Usb X. Then rename your email ‘TrueCrypt pdf file’ into whatever you said you would name the file during ‘Method 6 (Variation 2): step 8.2. The sample file name from the example in Method 6 (Variation 2): step 1 is ‘_____’.
Step 13.2: Turn on your computer in your normal computer operating system (in our case it is Windows 7), as we will now be connecting to the internet. Alternatively, you can create another Linux usb operating system using yet another unrelated usb drive and then use this to connect to the internet. Doing it this way offers slightly more security since your TrueCrypt pdf file cannot be exposed to malware that may be on your regular computer operating system when the usb containing the files are initially inserted. Do note that you absolutely cannot use the Zorin OS operating system on Usb No. 9 to connect to the internet as it contains sensitive data. Note that you are not advised use the Zorin OS operating system on Usb X to connect to the internet as we will be using it later (in method 6: variation 2: steps 15.5 – 15.6) to format a usb drive and don’t want to possibly compromise it by connecting to the internet (although it is alot less risky than using Usb No. 9 and probably less risky than using your regular computer operating system – Windows 7 in our case). If you do use the Linux usb operating system to connect to the internet, then remember to format the usb drive afterwards (by following Method 4: steps 15.12 – 15.14 for the usb drive).
To connect to the internet using the Zorin OS usb operating system, on the bottom right hand side of the screen select the icon that allows you to connect to the internet. Then read and follow the italicized and bold "Additional Information" notes at the end of Method 3, 4 or 5 for a guide on how to securely connect to the internet). After this, select your connection and connect to the internet.
Step 13.3: Login to your email account, create a new email and upload the email ‘TrueCrypt pdf file’. Carefully type in all the email addresses which you own and want to send it to (the list should be in the new Text File you created in Step 11.10); type in the subject line whatever you said you would type in Method 6 (Variation 2): step 8.2. The sample subject line text from the example in Method 6 (Variation 2): step 1 is ‘____’.
Step 13.4: Type in the email text whatever you said you would type in Method 6 (Variation 2): step 8.2. The sample text in the email from the example in Method 6 (Variation 2): step 1 is:
‘Please, please do not delete or save onto your computer. Please only open if allowed, using the password in my safe deposit box. The information on this usb is strictly for your viewing only and is strictly for storage here’.
Step 13.5: Double check all the details are correct and then hit send to send the emails.
Congratulations, your ‘TrueCrypt pdf file’ with the ‘password protected pdf file’ containing the ‘coded instructions’ from Method 6 (Variation 2): step 2 has been successfully emailed
Step 14: Finalise and store the safety deposit box usb in bank safe deposit box
Step 14.1: Take your completed ‘safety deposit box usb’ and completely wrap it in several layers of plastic (food) wrap. Then completely wrap it in several layers of aluminum foil. This material will completely shield the usb from Electromagnetic pulses (EMP) which may damage or render the usb useless.
Step 14.2: Now repeat step 14.1 to make it extra safe against EMP pulses.
Step 14.3: Place your foil/plastic wrapped master usb into the hard usb case.
Step 14.4: Label the usb case or the outside of the usb with something like:
“VERY IMPORTANT INFO INSIDE: PLEASE OPEN!”
You can do this by printing it out onto paper and then attaching it to the usb or usb hard case with sticky tape.
Step 14.5: Put your Master usb in the bank safety deposit box.
You should be aware that it is unknown how long your usb flash drive will accurately retain its data when not accessed in this way. No one can really know for sure as the technology was only invented sometime between the year 1995-2000. SanDisk quote 10 years data retention on their datasheets. We believe that this period is longer (in the vicinity of 100+ years) but recommend that you rewrite or replace the buried usb drive at least once every 10 – 15 years. SanDisk do however offer a product called ‘SanDisk Memory Vault’ that quotes a data retention period of 100 years, so you can use this as an additional backup to store also, if you prefer.
It is also recommended you create a duplicate safety deposit box usb and store it in another bank safety deposit box in case something happens to your first one. In this case you will need to prepare more master usb’s each from the beginning of Method 5: step 2; you cannot simply copy and paste all the files onto another usb drive.
Congratulations, you have placed the safe deposit usb in the bank safety deposit box
Step 15: Delete all remaining ‘TrueCrypt pdf file’ copies from all storage mediums after ensuring you have a sufficient number of smaller TrueCrypt pdf files (see the italicized 7th and 8th points of Method 5 Guidelines for details), and then format all unnecessary usb drives
Step 15.1: Re-boot your computer into the Linux usb operating system on Usb No. 9 (see method 3: step 3 if you don’t remember how to do this). Then create a sufficient number of smaller TrueCrypt pdf files (version A) so you can access and use the bitcoins stored in them without having to dig up your buried Master usb. See the italicized 7th and 8th points of Method 5 Guidelines for details. If you like, you can choose to not create these smaller TrueCrypt pdf files (version A) and just keep the single TrueCrypt pdf file (version A) and store this instead.
Now transfer the TrueCrypt pdf file or files onto yet another usb drive that has been pre-formatted. You can use the Linux usb operating system to completely format the usb drive first if it hasn’t yet been pre-formatted (see method 6: variation 2: Step 15.3 for an example of how to do this). This usb drive will serve as the final resting place of the TrueCrypt pdf file/s. Alternatively, you can also transfer the file/s to an external hard drive as a second backup. Be very careful to ONLY transfer the TrueCrypt pdf file/s and be careful not to transfer them onto any of your main computer hard drive/s where your regular computer operating system is (Windows 7 in our case). Storing it on your main computer hard drive/s will make it more accessible to online hackers. If you accidently make a mistake and transfer any unsecured LibreOffice or other files then you need to restart this method from the beginning of Method 3: step 1.
If you don’t have an extra usb drive available, then you can temporarily store the file on ‘Usb X’ by inserting ‘Usb X’ into a free usb port and copying and pasting the files over from your desktop. Do note though that doing it this way will require more work later on. Basically, at the next immediate opportunity in Method 6: variation 2: OPTIONAL STEP 15.4, once Usb No. 10 has been completely formatted in the Zorin OS usb operating system, you will need to load up your computer again in your regular operating system (Windows 7 in our case) and format Usb No. 10 using the ‘Eraser’ program before loading your computer in the Zorin OS operating system again and storing the password protected files in the final resting place of Usb No. 10 (Method 6: VARIATION 2: OPTIONAL STEP 15.4 gives exact instructions of how to do this).
Step 15.2: OPTIONAL STEP: Carefully transfer the electrum wallet file/s you created in Method 3: Step 5 onto your main operating system’s (Windows 7 in our case) electrum wallet folders (if you don’t still have a copy of these then you can create new one/s using the seeds from the TrueCrypt pdf file). It is possible to transfer the wallet files from within the Linux usb operating system by first mounting the drive containing the electrum wallet folders (usually drive C).
Zorin OS: Click ‘Z’ menu bar icon on bottom left hand side of desktop > select ‘Documents’ > scroll down to ‘+ Other Locations’ and click it > click on the drive containing the electrum wallet folders to mount the drive (usually drive C although the name of the drive will not be visible, only its size) > open the correct folder (usually C: \Users\ Name_of_your_computer\ AppData\ Roaming\ Electrum\ wallets) > copy and paste the wallet files into this folder.
Your main operating system’s (Windows 7 in our case) electrum wallet folders were created when and if you completed Method 2 (when we installed the electrum desktop program ‘electrum-2.7.18-setup.exe’ into the main operating system (Windows 7 in our case)). If you prefer instead to transfer the wallet files created in Method 3: Step 5 while using your regular computer operating system (in our case Windows 7), then see the instructions immediately before Method 2: Step 4 for details of how to do this. Bear in mind however that transferring the file using the main operating system (in our case Windows 7) has slightly more risk since the wallet files may be more exposed to malware on your regular operating system when the usb containing the files are initially inserted.
Step 15.3: Completely format Usb No. 10 within Zorin OS by doing the following:
Insert Usb No. 10 into a free usb port. In the Zorin OS operating system desktop, take notice of the name of the new drive that appears. In our example case it is ‘2.1 GB Volume’. Click the ‘Z’ menu bar icon on bottom left hand side of desktop. Then click ‘Documents’. Now scroll down to the part that shows the usb drive you just inserted. The name should match the name of the drive on your desktop. In our example case it is ‘2.1 GB Volume’. The drive should have the mark that looks like an upwards facing arrow immediately on the right hand side of it which shows that the drive has been mounted.
You will first be doing a quick format and then later a full format of all the data on this usb drive. For the quick format, right click this drive ‘2.1 GB Volume’, then click ‘Format’. In the screen that appears leave everything at the default setting:
Erase: Don’t overwrite existing data (Quick)
Type: Compatible with all systems and devices (FAT)
Then click ‘Format...’. On the next ‘Are you sure you want to format the volume?’ screen that appears, click ‘Format’.
Now for the full format, right click this drive ‘2.1 GB Volume’ again, and then click ‘Format’. In the screen that appears change the first part beside ‘Erase’ so you have the following settings:
Erase: Overwrite existing data with zeroes (Slow)
Type: Compatible with all systems and devices (FAT)
Then click ‘Format...’. On the next ‘Are you sure you want to format the volume?’ screen that appears, click ‘Format’.
Now wait up to 10 minutes for your computer to completely format the usb drive. While it is doing this, no indication that this is happening will show on your screen but rest assured your computer is formatting the drive. Once the drive has been completely formatted, the usb will reappear on your screen (not the desktop). On our screen it shows ‘2.1 GB Volume’ again. This is how you will know the format has been completed.
Step 15.4: OPTIONAL STEP: ONLY DO THIS STEP IF YOU HAVE TEMPORARILY STORED THE TRUECRYPT PDF FILE OR FILES ON USB X DURING STEP 15.1.
Switch off your computer. Then boot up your computer in your regular operating system (Windows 7 in our case). After this insert Usb No. 10 into a free usb port and do a quick format of Usb No. 10 (a quick format should be done and NOT a complete format). Windows 7: Right click usb drive > click ‘Format…’ > click ‘Start’ > click ‘OK’. After this, do a complete ‘Eraser’ format of Usb No. 10. This process can take a while so be patient. Windows 7: Right click usb drive > select ‘Eraser’ > click ‘Erase Unused Space’. Switch off your computer, Insert Usb No. 9 which still contains the Linux usb operating system (Zorin OS or Linux Mint) and boot up your computer in this Linux usb operating system. Now insert Usb X into a free usb port and copy and paste the password protected files onto your Linux usb operating system desktop. Finally insert Usb No. 10 again and copy and paste these same password protected files from the desktop onto the final resting place which is Usb No. 10. Double check that the files have been transferred properly.
Step 15.5: Switch off your computer. Insert Usb X which is the second newly created Linux usb operating system that was prepared in Method 3: Step 2.8, and boot up your computer in the Zorin OS Core or Linux Mint (Linux based) usb operating system using Usb X.
Step 15.6: Completely format Usb No. 9 within Zorin OS by doing the following:
Insert Usb No. 9 into a free usb port. In the Zorin OS operating system desktop, take notice of the name of the new drive that appears. In our example case it is ‘2.1 GB Volume’. Click the ‘Z’ menu bar icon on bottom left hand side of desktop. Then click ‘Documents’. Now scroll down to the part that shows the usb drive you just inserted. The name should match the name of the drive on your desktop. In our example case it is ‘2.1 GB Volume’. The drive should have the mark that looks like an upwards facing arrow immediately on the right hand side of it which shows that the drive has been mounted.
You will first be doing a quick format and then later a full format of all the data on this usb drive. For the quick format, right click this drive ‘2.1 GB Volume’, then click ‘Format’. In the screen that appears leave everything at the default setting:
Erase: Don’t overwrite existing data (Quick)
Type: Compatible with all systems and devices (FAT)
Then click ‘Format...’. On the next ‘Are you sure you want to format the volume?’ screen that appears, click ‘Format’.
Now for the full format, right click this drive ‘2.1 GB Volume’ again, and then click ‘Format’. In the screen that appears change the first part beside ‘Erase’ so you have the following settings:
Erase: Overwrite existing data with zeroes (Slow)
Type: Compatible with all systems and devices (FAT)
Then click ‘Format...’. On the next ‘Are you sure you want to format the volume?’ screen that appears, click ‘Format’.
Now wait up to 10 minutes for your computer to completely format the usb drive. While it is doing this, no indication that this is happening will show on your screen but rest assured your computer is formatting the drive. Once the drive has been completely formatted, the usb will reappear on your screen (not the desktop). On our screen it shows ‘2.1 GB Volume’ again. This is how you will know the format has been completed.
Step 15.7: Boot up your computer in your regular operating system (in our case Windows 7).
Step 15.8: Do a quick format of Usb No. 10 (a quick format should be done and NOT a complete format). Windows 7: Insert Usb No. 10 into free usb port > right click usb drive > click ‘Format…’ > click ‘Start’ > click ‘OK’. (SKIP THIS STEP IF YOU HAVE ALREADY DONE METHOD 6: VARIATION 2: OPTIONAL STEP 15.4).
Step 15.9: Do a complete ‘Eraser’ format of Usb No. 10. This process can take a while so be patient. Windows 7: Right click usb drive > select ‘Eraser’ > click ‘Erase Unused Space’. (SKIP THIS STEP IF YOU HAVE ALREADY DONE METHOD 6: VARIATION 2: OPTIONAL STEP 15.4).
Step 15.10: Do a quick format of Usb No. 9 (a quick format should be done and NOT a complete format). Windows 7: Insert Usb No. 9 into free usb port > right click usb drive > click ‘Format…’ > click ‘Start’ > click ‘OK’.
Step 15.11: Do a complete ‘Eraser’ format of Usb No. 9. This process can take a while so be patient. Windows 7: Right click usb drive > select ‘Eraser’ > click ‘Erase Unused Space’.
Step 15.12: Do a quick format of Usb X (a quick format should be done and NOT a complete format). Windows 7: Insert Usb X into free usb port > right click usb drive > click ‘Format…’ > click ‘Start’ > click ‘OK’.
Step 15.13: Now do a complete format of Usb X (a complete format should be done now and not a quick format). Windows 7: Right click usb drive > click ‘Format…’ > Uncheck ‘Quick Format’ > click ‘Start’ > click ‘OK’.
Step 15.14: Finally do a complete ‘Eraser’ format of Usb X. This process can take a while so be patient. Windows 7: Right click usb drive > select ‘Eraser’ > click ‘Erase Unused Space’.
Congratulations, you have completed Method 6 (Variation 2)
ADDITIONAL INFORMATION