"The best bitcoin is the one you store yourself"
Security Level = VERY HIGH
BEFORE WE START
You might be asking, if we can simply bury somewhere in our backyard a usb containing the ‘TrueCrypt pdf file’ exactly as it is instead of preparing it in this long drawn out process. Surely it should be sufficient and adequate for future retrieval? Once again, like our comments in Method 4, the short answer to this question is: it is entirely up to you but we strongly recommend you follow our instructions to bury it.
When you bury a usb, it is quite a long and tedious process in itself and in our experience once you have done it once, you don’t really want to have to ever do it again even if there are many benefits to doing so. Also, every additional time you bury it is another chance someone may notice. If you follow our process completely the first time around it may take a little longer than it otherwise would, but you can be confident that you have covered most of your bases and prevented most problems that may arise from not burying it using our steps.
GUIDELINES
**********************************************************************************************************************************************************************************
**********************************************************************************************************************************************************************************
HOW TO DO IT

***Go to www.bitgoldwallet.com for information on what bitcoin is and how to safely buy, use and store it, and how to choose a secure and memorable password (like the one that may have been used to secure these files). Its Method 5 section also has a copy of these instructions below***
NOTE TO READER
This USB drive gives you real access to all the Bitcoins I own! Bitcoins are like real money and must be treated as such. Do not allow anyone else access to this usb drive or any files on it at anytime.
Before taking any action you MUST do the following in this exact order to guarantee that you know enough about Bitcoin to start accessing it safely. Making a mistake could cause you to lose ALL these bitcoins to an accident or to theft.
1. Copy and paste this ‘IMPORTANT INSTRUCTIONS…’ document as well as all ‘TrueCrypt pdf files’ on this usb onto your main computer hard drive. Also copy and paste all these to another storage medium as a second backup such as a usb drive or an external hard drive. Try not to accidently delete these files but if you do, do not stress cos all is not lost since another copy of these exist elsewhere on this usb. If you accidently delete these then move onto instruction 2, but remember to copy and paste these files to your main computer when you next get the chance.
2. Go to www.bitgoldwallet.com and read all the articles about bitcoin on the ‘Intro’ section. Get an idea of what it is. Then do an online search to see what the current price per bitcoin is.
3. Look at Method 2 on www.bitgoldwallet.com . Read the entire article and then complete Method 2: steps 1-4 to install Electrum software on your main computer. Create the first wallet file so you know how they work.
4. If there is a ‘Public Addresses Only’ pdf file on this usb, create a ‘watching only’ wallet in the Electrum software you just installed on your main computer. You will soon find out exactly how many bitcoins we have and can estimate what they are worth. To create the watching wallet: Open ‘Electrum program> press ‘File’ > press ‘New/Restore’ > click ‘OK’ > select ‘Watch Bitcoin addresses’> copy and paste all public addresses from pdf file into Electrum program > click ‘Next’ > click ‘OK’.
5. Now you should know what all the Bitcoins are worth. If you still don’t know, then go back to steps 2-4 and do it again. This is important. Also know that there is a chance that I have more bitcoins which are not in these addresses but which can be viewed by opening the encrypted files on this usb and then creating ‘watching only’ wallets using the ‘master public keys’ in the password protected pdf file, instead of from the ‘Public-Addresses-Only’ pdf file.
6. Now go to www.bitgoldwallet.com and using 3 completely different usb drives (DO NOT use this one), do Method 3: steps 1.1-1.7, then Method 4: step 1.1, then Method 5: step 1.2, then Method 3: steps 2.1–4.3, then Method 4: steps 3.1- 3.8. These steps will show you how to create a Linux usb operating system which you need to create and use everytime you want to securely access the ‘TrueCrypt pdf files’.
7. You are now almost ready to open the password protected encrypted TrueCrypt folders and pdf files which contain all my electrum seed words, seed extension words, bitcoin public and bitcoin private keys. Before we do this though, complete Method 3: steps 9.5-9.7 & 9.10 -9.12. These steps show you what you need to do everytime, after you have accessed the ‘TrueCrypt pdf files’. Basically, you need to completely and thoroughly delete both usb drives. You will need to format and delete ‘this’ usb drive as well after you have used it for the first time.
8. You are now ready to access the TrueCrypt pdf file on this usb using the Linux usb operating system that is installed on this usb. You must stay disconnected from the internet for the entire time you are using this Linux based usb operating system. Once you have opened the TrueCrypt pdf file, you can create a wallet file using electrum portable by using the ‘seed’ words and ‘seed extension’ words. In Linux Mint: Double click ‘electrum portable’ program > click ‘File’ > click ‘New/Restore’ > enter new name > click ‘OK’ > select ‘Standard wallet’ > click ‘Next’ > select ‘I already have a seed’ > click ‘Next’ > click ‘Options’ > select ‘Extend this seed with custom words’ > click ‘OK’ > enter ‘seed’ words > click ‘Next’ > enter ‘seed extension’ words > click ‘Next’ > enter a strong password into both boxes > click ‘Next’.
ALWAYS add a strong password when it asks you to enter one. See the notes below after “Electrum portable’ software:” in this ‘IMPORTANT INSTRUCTIONS…’ document for advice on what to do afterwards with your newly created electrum wallet files in order to use them.
This usb drive has the following files installed and ready to use:
Linux Mint usb operating system: Use this usb operating system to view all the password protected files on this usb for the first time. This Linux Mint usb drive operating system is a one time use only and once the password is entered, it should be considered ‘used’ and must not be reused after shutting down the computer. Only the TrueCrypt pdf file and other files on the usb should be reused and re-accessed using a newly created Linux usb operating system.
To view the files on this usb, you need to boot up the usb in your computer by:
1. Connecting this usb to one of your usb ports (ideally the fastest port -UBS3 if available), and then turning on the computer.
2. Waiting for the system to boot up automatically (works for some computers). If this doesn’t happen then restart your computer again and immediately press ‘F12’ repeatedly as it is booting up. This should allow you to either change the boot device order to have the removable usb drive load first, or to select a preferred boot device. In either case, select this usb drive as the boot device. If pressing ‘F12’ doesn’t work then restart your computer again and this time repeatedly press ‘Escape’. This step should allow you to boot up this usb on your computer.
After the usb is booted, all of the following files will be on the Linux Mint usb operating system’s desktop. Simply click on these to use.
This usb drive contains the following files:
TrueCrypt pdf file (version A): Make sure you create backups of this file on at least 2 different computer devices as soon as you can. This TrueCrypt pdf file (version A) contains the ‘password protected pdf file’ that contains the information to access all my Bitcoins. In the password protected pdf file is all my electrum seeds, and bitcoin public and private addresses of all my bitcoins. Note that you should load the addresses from the Electrum seeds rather than from the private addresses if you plan to use them, since there may be more addresses which haven’t been recorded on the pdf document which were generated and used afterwards by the software.
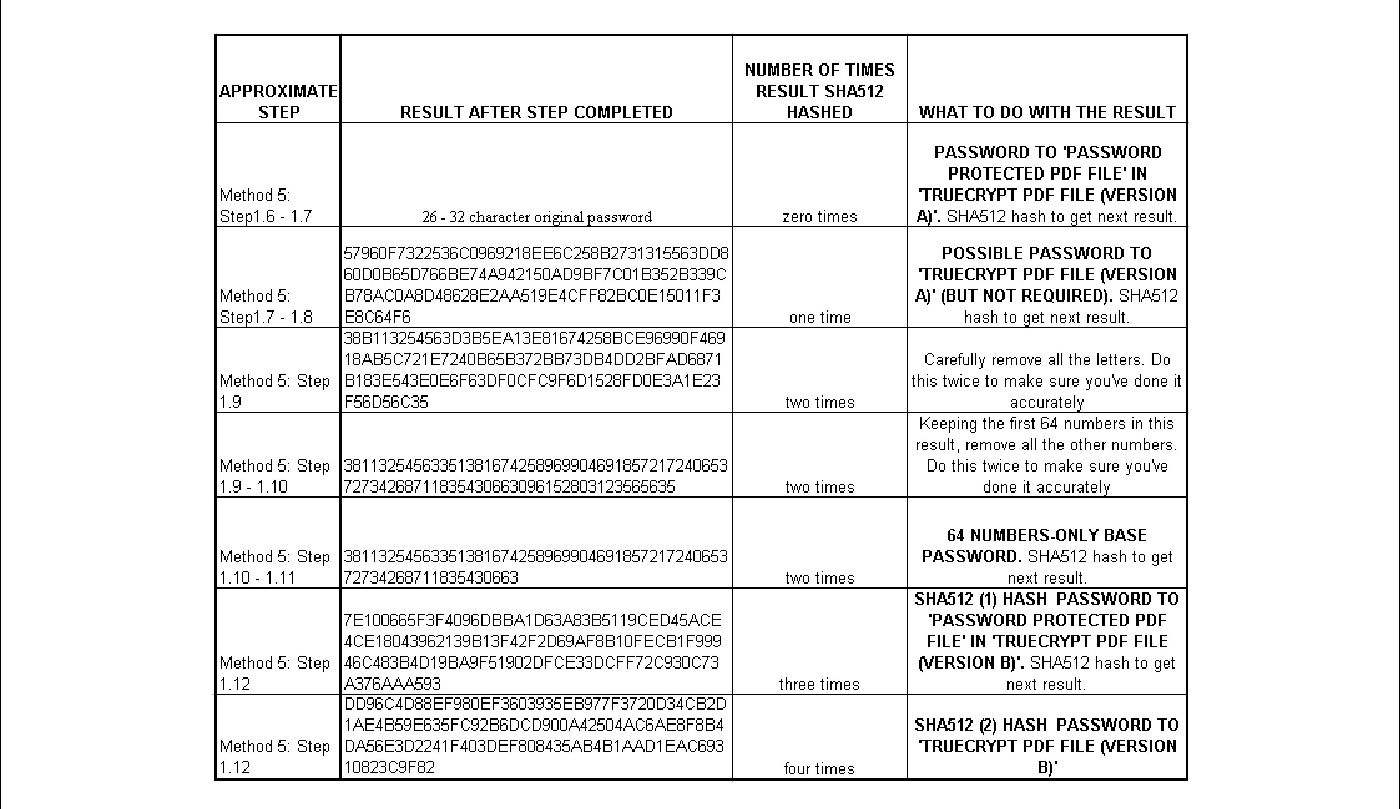
To open the ‘password protected pdf file’ use your 26 - 32 character password.
To open the ‘TrueCrypt pdf file (version A)’ file though you may need to use ‘QuickHash-Windows-v2.6.9.2’ to create a SHA512 hash of the 26 – 32 character password and use that SHA512 hash to open the TrueCrypt pdf file (version A) first. Try this if you can’t gain access with only the 26 – 32 character password.
TrueCrypt pdf file (version B): Make sure you create backups of this file on at least 2 different computer devices as soon as you can. This TrueCrypt pdf file (version B) contains the ‘password protected pdf file’ that contains the information to access all my Bitcoins. In the password protected pdf file is all my electrum seeds, and bitcoin public and private addresses of all my bitcoins. Note that you should load the addresses from the Electrum seeds rather than the private addresses if you plan to use them, since there may be more addresses which haven’t been recorded on the pdf document which were generated and used afterwards by the software.
To open both these files use your 64 digit numbers-only password. If entering it directly for all the files doesn’t work then use ‘QuickHash-Windows-v2.6.9.2’ to create a SHA512 hash of these 64 numbers. Then create a SHA512 hash of this result. The second SHA512 hash result will be the TrueCrypt pdf file (version B) volume password. The first SHA512 hash result will be the password to the ‘password protected pdf file’ within the TrueCrypt pdf file (version B) volume.
QuickHash-Windows-v2.6.9.2: This program will create the SHA512 hash to produce your required password to the TrueCrypt pdf file. In Linux Mint: Open ‘QuickHash-Windows-v2.6.9.2’ folder on desktop > double click ‘QuickHash-Windows-x86-v2.6.9.2’ > select ‘SHA512’ > then start using.
truecrypt-7.1a-linux-x86.tar.gz: This program is needed to open the TrueCrypt pdf file, by mounting it first on a virtual drive. In Linux Mint: Click ‘Menu’ on the bottom left hand side of the desktop > search ‘truecrypt’ in the search bar > click on the ‘TrueCrypt’ option that appears > click ‘Select File...’ > search for ‘TrueCrypt pdf file’ on usb drive > select ‘TrueCrypt pdf file’ by pressing on it> click ‘Open’ > click on any ‘Slot’ (1-64) on the main menu > click ‘Mount’ > Enter the password (see QuickHash-Windows-v2.6.9.2 notes and TrueCrypt pdf file notes above to see what the correct password is) >click ‘OK’ .
Once mounted: In Linux Mint: Open the folder that opened automatically but if one doesn’t open automatically, search for the new folder that just appeared on the Linux Mint desktop (named as ‘thefilesize+Volume’) and double click on that > then double click the password protected pdf document within > enter password > then click ‘Unlock Document’ to view the document.
Once you have finished using all the programs: In Linux Mint: click ‘Dismount All’ on the TrueCrypt main menu > Press ‘Exit’.
‘Public Addresses Only’ pdf file: This pdf document contains the public addresses (and not private addresses or electrum seeds) of most (if not all) of my bitcoins. Use this document if you want to view the public addresses I own and see the funds in it by creating a ‘watching only’ wallet using Electrum software: Open ‘Electrum’ program > press ‘File’ > press ‘New/Restore’ > click ‘OK’ > select ‘Watch Bitcoin addresses’ > copy and paste all public addresses into Electrum program > click ‘Next’ > click ‘OK’.
‘Electrum portable’ software: This program is the Bitcoin software you should use to create your bitcoin wallets from the seed words and seed extension words on the TrueCrypt pdf file/s. To run the program: while within the Linux Mint usb operating system, insert an empty usb into your computer usb port, then copy and paste the whole ‘electrum portable’ program onto the usb, then double click the electrum portable program and run it off the usb. Always include a strong password when creating an electrum wallet from a seed or from bitcoin private addresses. After creating the wallet file, in order to start using it, restart your computer in a newly created Linux usb operating system, and then load the electrum portable program again from the usb. Following this, connect to the internet from a mobile device using USB tethering after setting a newly chosen random password for that connection, and then complete your bitcoin transactions. Ideally the mobile device or phone you use to connect to the internet with, will have just had a factory reset done, although this is not strictly required for most everyday users (consider using an old phone you have lying around solely for this purpose though). After doing all this, completely format/delete all the files on all the usbs while still within the Linux usb operating system (by doing a full format of the usb's).
***Go to www.bitgoldwallet.com for information on what bitcoin is and how to safely buy, use and store it, and how to choose a secure and memorable password (like the one that may have been used to secure these files). Its Method 5 section also has a copy of these instructions above***
>>> End of Doc <<<
Step 4.2: Save the file and name it ‘IMPORTANT INSTRUCTIONS FROM (your_name) – READ HERE’. Put your name in the file name in capital letters where it says ‘(your_name)’ so whoever sees it knows it is from you. Then copy and paste it onto Usb No. 6.
Use your common sense and make sure you do the actual burying at a time and place where it is unlikely anyone will see you. Also choose a good location such as your backyard or if you have alot of bitcoins, away from your main place of residence and in a secondary place of residence which you own. Also take into account possible environmental disasters such as floods, hurricanes or forest fires which may cause you to lose your buried usb’s. Strongly consider burying it in more than one place to mitigate all these risks (in which case you will need to prepare more master usb’s each from the beginning of step 2; you cannot simply copy and paste all the files onto another usb drive).
ADDITIONAL INFORMATION
How to Access Your Bitcoins:
How to Transact With Your Bitcoins:
Other Information:
***** 2024 UPDATE: CRITICAL UPDATE COMING SOON *****
To obtain the maximum level of security possible, a new section is currently being prepared that will show users how to use the above method on a newly purchased completely offline computer that will only be ever used to create your bitcoin keys and wallets and to sign your bitcoin transactions. This will be a dedicated offline computer used only for bitcoin purposes. Every single time, before the computer is switched on, users will need to open the computer up and disconnect and then put back in all the RAM cards to reset the system. The sound and network cards, as well as the microphone of this offline computer will be physically removed permanently (not just disabled), and the computer will never ever be connected to the internet. If possible, also remove the connected hard drive and also regularly replace the mouse and keyboard that is used with this computer to prevent compromised malware from hijacking your operating system. Additionally, this offline computer will never have any usb’s connected to it except during the initial installation or when retrieving stored bitcoin data from the dedicated storage usbs. All transfers of information (in the form of master public keys, raw transaction text and signed transaction text) from this offline computer to your online computer and vice versa will be via QR code images captured on the completely offline computer using an external webcam that is connected only when used. This new section will replace Windows 7 with Windows XP as the initial operating system. Zorin OS will remain the usb operating system however instructions on how to create a Zorin OS Live CD will be included for extra security and convenience. And so too will instructions on how to transfer the encrypted bitcoin files onto a CD/DVD for permanent, less alterable storage. These measures are designed to eliminate the ever present danger of malware infecting your computer and/or usb’s and compromising your bitcoin security. Click here for details...
**************************************************************************************************************************************************************
All Work-in-progress / Planned additions or Alternate steps to Method 5, which will be in this New section are currently shown in BLUE font on this ‘Method 5 (Deep cold storage) webpage.
**************************************************************************************************************************************************************